Security Trends in 2017 – ISC2 report – Threat Monitoring Intelligence Management
CYBERSECURITY TRENDS
Latech, فناوری لاجورد تکوین, لاتک
2017 SPOTLIGHT REPORT
Latech, فناوری لاجورد تکوین, لاتک
PRESENTED BY (ISC)2
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
OVERVIEW
Latech, فناوری لاجورد تکوین, لاتک
The cybersecurity landscape is changing rapidly, making current and actionable guidance on the latest trends more important than ever.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, فناوری لاجورد تکوین, لاتک
Intro to general trends in ISC2 report:
http://lajvardtech.com/en/security-trends-in-2017-isc2-report-general-trends/
Latech, فناوری لاجورد تکوین, لاتک
THREAT MONITORING, INTELLIGENCE & MANAGEMENT
Latech, فناوری لاجورد تکوین, لاتک
Cybersecurity is about preventing, detecting and remediating external and internal threats facing enterprises and government organizations, ranging from malware and phishing attacks to threats posed by trusted insiders. A variety of tools have emerged to address these threats—from unified threat management platforms, better threat intelligence solutions for greater visibility across the IT environment, and automatic threat hunting, detection and remediation products to help with emerging and advanced threats.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
TOP CHALLENGES FOR SOCS
Latech, فناوری لاجورد تکوین, لاتک
The top two challenges facing SOCs are the detection of advanced threats (hidden, unknown, and emerging) and the lack of expert security staff to mitigate such threats. More than half of the SOCs face these two top challenges. All the challenges mentioned in the survey were ranked by at least 30% of the participants, suggesting that SOCs are dealing with a broad array of issues on a day-to-day basis.
Q: Which of the following do you consider to be top challenges facing your SOC?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
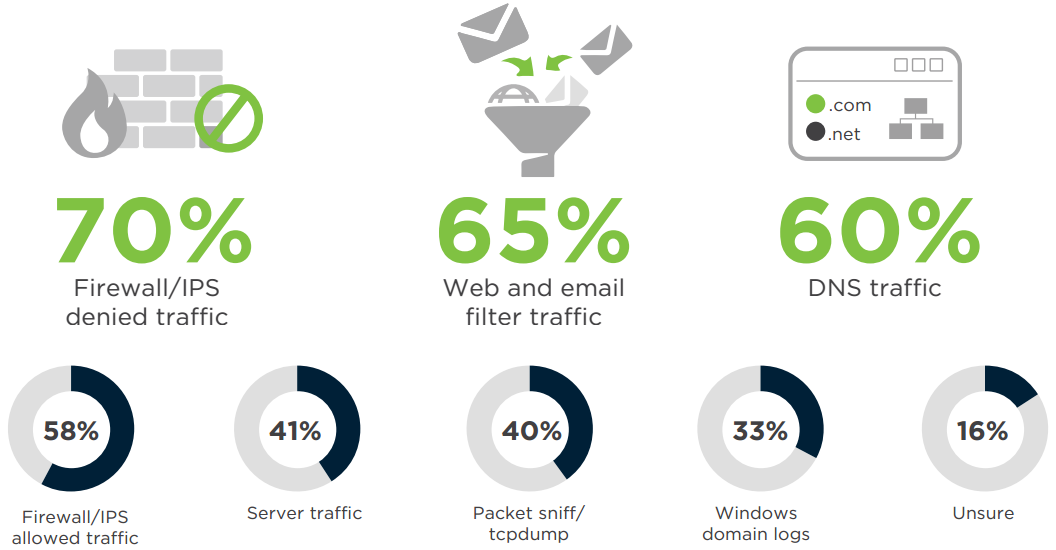
DATA CAPTURED FOR FORENSIC REVIEW
Latech, فناوری لاجورد تکوین, لاتک
When asked about the type of data their SOC log for forensics review, three in four respondents said they log and review firewall/IPS denied traffic. Other commonly collected logs are firewall/IPS allowed traffic, DNS traffic, and Web and email traffic. The importance respondents see in keeping different types of logs for forensic review is evident by the fact that each data option was logged by at least 30% of the respondents.
Q: What kind(s) of data does your SOC log for forensic review later?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
ATTACK DISCOVERY
Latech, فناوری لاجورد تکوین, لاتک
Attackers dwell on a network for an average of 40 days before they’re discovered, according to the survey. Some respondents said attackers were discovered much faster while others said the attack could go undetected for as long as three months or even longer. Nearly all respondents agree that attackers dwell on a network for some period of time before they’re discovered by the SOC.
Q: On average, how long do attackers who breach your security defenses dwell in your network before they are discovered by your SOC?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
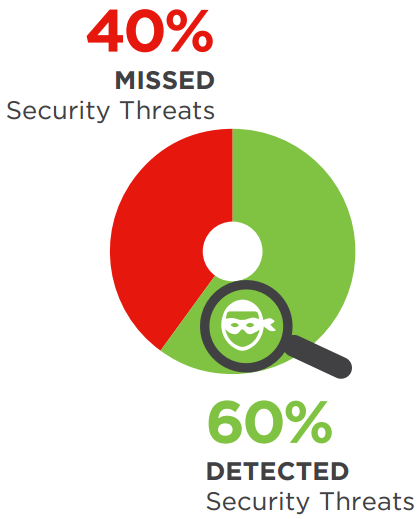
An average of 40% of security threats to the respondent’s SOC are missed, while an average of 60% were identified. With over 4 in 10 security threats being missed by SOCs, there’s significant potential for a breach.
Q: Missed and Detected Security Threats?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY,DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
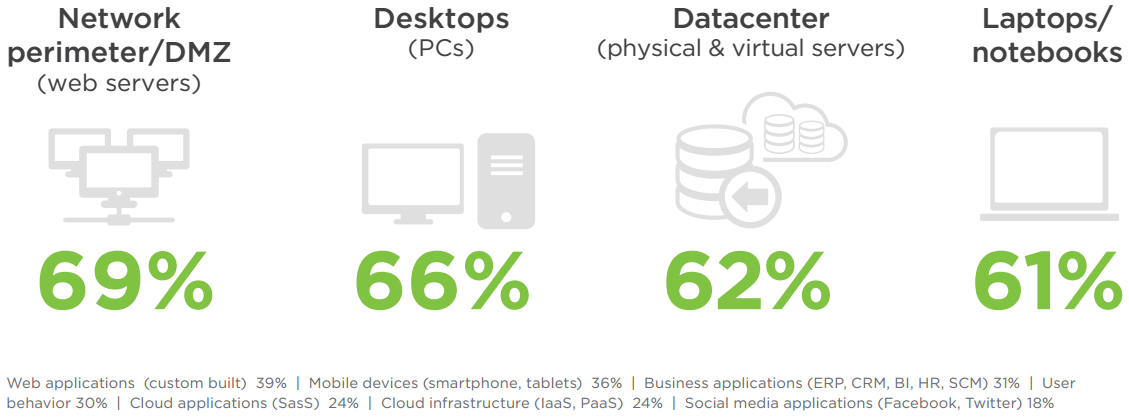
IT SYSTEMS MONITORING
Latech, فناوری لاجورد تکوین, لاتک
Monitoring of sensitive systems and users for suspicious behavior is a key component of robust security frameworks. The most commonly monitored IT layer is the network (69%) followed by endpoints (PCs 66%/laptops 61%) and servers in the datacenter (62%).
Q: What IT systems do you routinely monitor for security risks?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
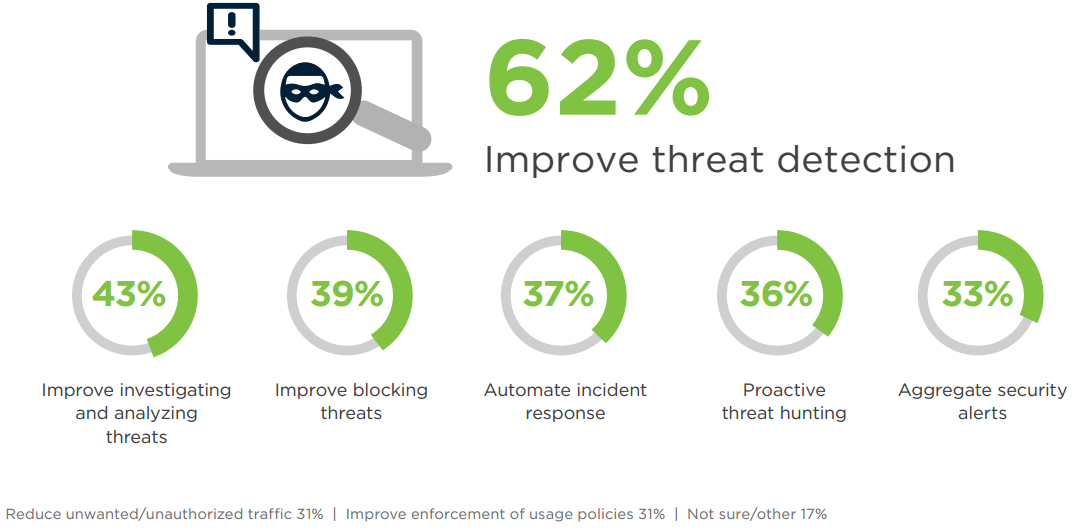
MOST CRITICAL CAPABILITIES
Latech, فناوری لاجورد تکوین, لاتک
What threat management capabilities are most important to organizations? Threat detection (62%) tops the list, followed by analytical capabilities (43%) and blocking threats (39%).
Q: What are the most critical threat management capabilities for your organization?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
BARRIERS TO THREAT MANAGEMENT
Latech, فناوری لاجورد تکوین, لاتک
In keeping with overall barriers to a more effective security posture, lack of skilled employees also tops the list of barriers to better threat management (33%).
Q: What is the most critical barrier holding your organization back from implementing threat management more effectively?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
THREAT INTELLIGENCE SOLUTIONS
Latech, فناوری لاجورد تکوین, لاتک
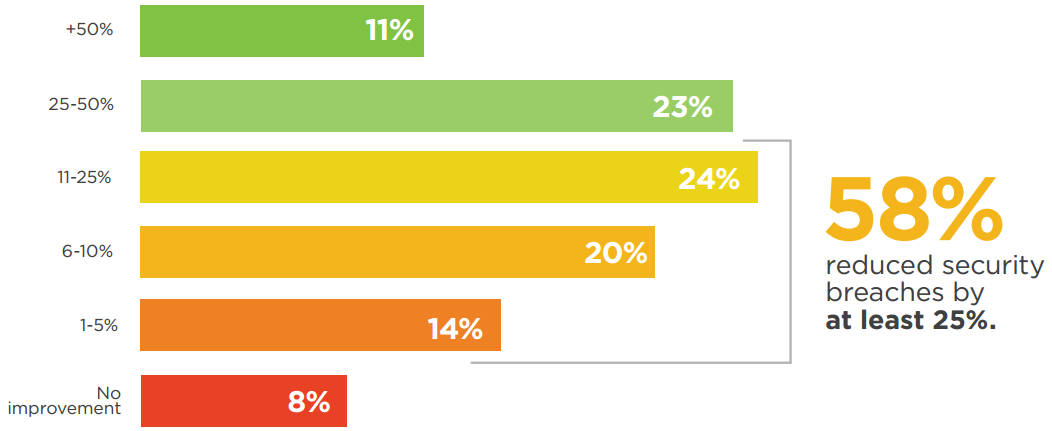
A majority of organizations (58%) estimate they reduced the number of security breaches by up to 25% by using threat intelligence solutions. Thirty-four percent reduced breaches by more than 25%. Eight percent of organizations saw no improvement.
Q: By what percentage have security breaches been reduced because of using threat intelligence solutions?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
CRITICAL SOC CAPABILITIES
Latech, فناوری لاجورد تکوین, لاتک
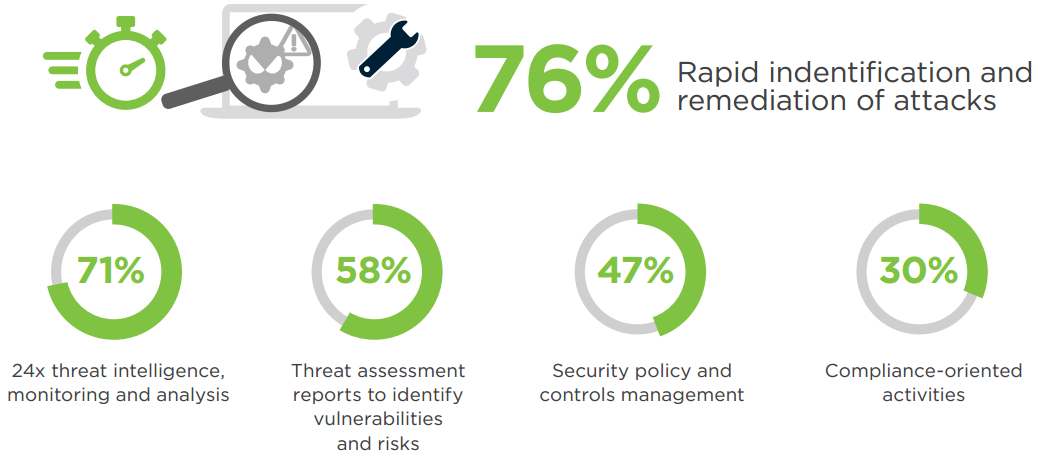
A Security Operations Center (SOC) is defined as an organized and highly skilled team whose mission is to continuously monitor and improve an organization’s security posture while preventing, detecting, analyzing, and responding to cyber security incidents with the aid of both technology and well-defined processes and procedures. Seventy-six percent of survey respondents agree that the most valuable SOC capabilities center around rapid identification and remediation of attacks.
Q: How valuable are the following capabilities in a SOC?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE
Latech, فناوری لاجورد تکوین, لاتک
Latech portfolio to meet requirements in Security Operation Center (SOC)
HPE ArcSight – Splunk – IBM QRadar – Tripwire
Latech, فناوری لاجورد تکوین, لاتک
Security trends in 2017
Latech, فناوری لاجورد تکوین, لاتک
Participants were engaged in survey in regards to below scopes:
Latech, فناوری لاجورد تکوین, لاتک