Security Trends in 2017 – ISC2 report – Application Security
CYBERSECURITY TRENDS
Latech, فناوری لاجورد تکوین, لاتک
2017 SPOTLIGHT REPORT
Latech, فناوری لاجورد تکوین, لاتک
PRESENTED BY (ISC)2
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, فناوری لاجورد تکوین, لاتک
Intro to general trends in ISC2 report:
http://lajvardtech.com/en/security-trends-in-2017-isc2-report-general-trends/
Latech, فناوری لاجورد تکوین, لاتک
OVERVIEW
Latech, فناوری لاجورد تکوین, لاتک
The cybersecurity landscape is changing rapidly, making current and actionable guidance on the latest trends more important than ever.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATION SECURITY
Latech, فناوری لاجورد تکوین, لاتک
Organizations across all sizes and industries are increasingly concerned about the security of their web applications, mobile applications, software packages such as ERP and other software. Application related breaches can lead to lost revenue, significant recovery expense, and loss of reputation. Thus, many organization implement incentives to prevent gaps in the security policy of an application or to avoid vulnerabilities in the underlying system that are could be caused by flaws in the design, development, deployment, upgrade, or maintenance or database of the application.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATIONS AT RISK
Latech, فناوری لاجورد تکوین, لاتک
According to Verizon’s recent security report, attacks on web applications are now the #1 source of data enterprise breaches, up 500% since 2014, causing cybersecurity professionals to be most concerned about customer facing web apps (50%) introducing security risk to the business. This is followed by mobile apps (41%) and desktop apps (34%) and business apps such as ERP platforms (29%).
Q: Which types of applications present the highest security risk to your business?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATION SECURITY CONCERNS
Latech, فناوری لاجورد تکوین, لاتک
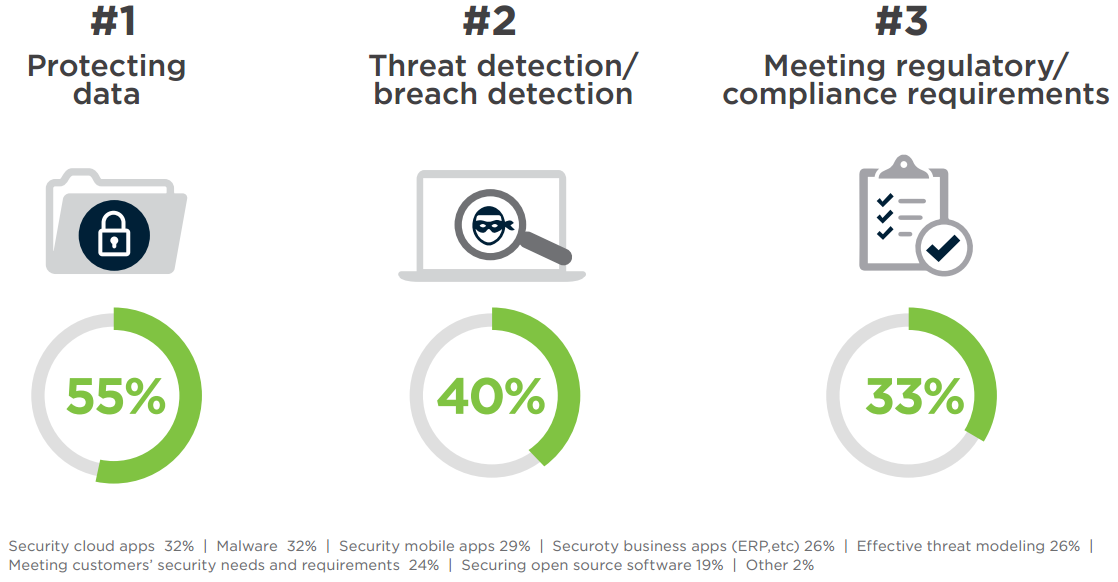
Protection of data (55%) tops the list of application security concerns, followed by detection of threats and breaches (40%) and meeting compliance requirements (33%).
Q: What are your top application security concerns?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATION SECURITY MATURITY
Latech, فناوری لاجورد تکوین, لاتک
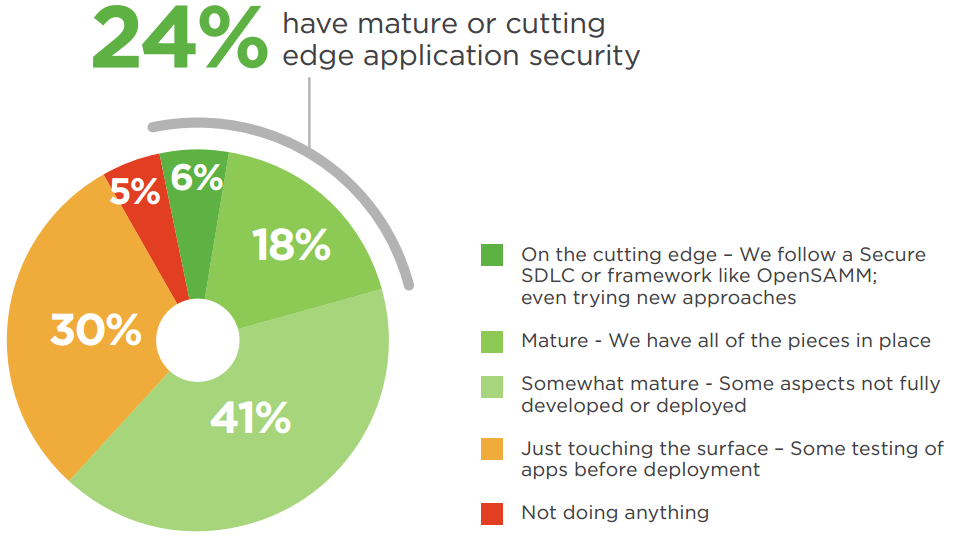
Only a small minority of organizations consider themselves at the cutting edge of application security (6%) or mature, with all critical application security controls in place (18%). The plurality of organizations feels only somewhat mature (41%) with key application security controls missing or just touching the surface (30%).
Q: Where do you think your company is in terms of the maturity of your application security strategy?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATION SECURITY TESTING
Latech, فناوری لاجورد تکوین, لاتک
Code reviews are the most common security testing control deployed by organizations (44%). This is followed by penetration testing, either conducted in-house (37%) or outsourced (33%). Application scanning during development (29%), QA or production (27%) round out the top five most common security testing controls.
Q: What application security testing do you have in place currently?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
APPLICATION SECURITY CHALLENGES
Latech, فناوری لاجورد تکوین, لاتک
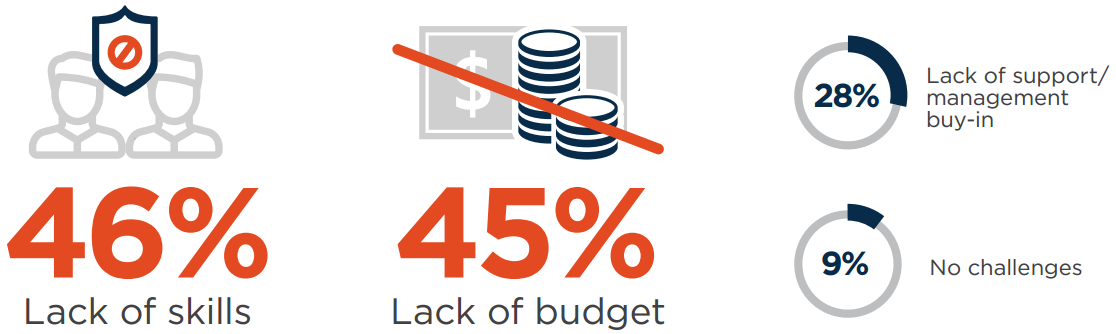
A recurring theme in our cybersecurity survey, the lack of security skills (46%) combined with a lack of budget (45%) are the biggest obstacles to implementing a robust application security program.
Q: What challenges do you face in implementing an application security program?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
PROTECTING BUSINESS APPLICATIONS
Latech, فناوری لاجورد تکوین, لاتک
Pentesting (59%) and security monitoring (58%) are leading the pack as the most popular measures to protect business applications.
Q: What application security measures are you taking in order to protect your business applications?
Latech, فناوری لاجورد تکوین, لاتک
Latech portfolio to meet requirements in Application Security
HPE Fortify – HPE WebInspect – Rapid7 AppSpider – CheckMarx
HPE LoadRunner – HPE UFT – PortSwigger BurpSuite
Latech, فناوری لاجورد تکوین, لاتک
Security trends in 2017
Latech, فناوری لاجورد تکوین, لاتک
Participants were engaged in survey in regards to below scopes:
Latech, فناوری لاجورد تکوین, لاتک