Security Trends in 2017 – ISC2 report – General trends
CYBERSECURITY TRENDS
Latech, فناوری لاجورد تکوین, لاتک
2017 SPOTLIGHT REPORT
Latech, فناوری لاجورد تکوین, لاتک
PRESENTED BY (ISC)2
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
OVERVIEW
Latech, فناوری لاجورد تکوین, لاتک
The cybersecurity landscape is changing rapidly, making current and actionable guidance on the latest trends more important than ever.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
KEY SURVEY FINDINGS
- With 54% of cybersecurity professionals anticipating successful cyberattacks on their organization in the next 12 months, it is no surprise that 52% are boosting their security budget by an average of 21%. The focus areas where companies will increase security spend include cloud infrastructure (33%) and cloud applications (28%). Training/education (23%) and mobile devices (23%) tie for the third spot.
- The three biggest obstacles to stronger cybersecurity are lack of skilled employees (45%), lack of budget (45%), and a lack of security awareness among employees (40%). To overcome these challenges and create a better security posture, 54% of organizations want to train and certify their current IT staff. Leveraging third-partner security solutions (47%), partnering with a managed service provider (41%), and hiring additional security staff (32%) are popular strategies companies use to address security issues.
- To better manage cyber threats and reduce the risk of a security breach, companies prioritize three key capabilities including improved threat detection (62%) followed by better analytical capabilities (43%) and threat blocking (39%). Fifty-eight percent of organizations estimate they reduced the number of security breaches by at least 25% using better threat intelligence and monitoring solutions.
- While cloud computing has become a mainstream delivery choice for applications, services and infrastructure, concerns about cloud security remain high. The top three cloud security concerns respondents need to address include protecting against data loss (57%), threats to data privacy (49%), and breaches of confidentiality (47%).
- As mobility and BYOD initiatives grow in the workplace, so do security concerns. Of biggest concern related to BYOD is data leakage or loss (69%), download of unsafe applications or content (64%), and the introduction of malware into the organization’s IT environment (63%).
- Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
GENERAL SECURITY TRENDS
Latech, فناوری لاجورد تکوین, لاتک
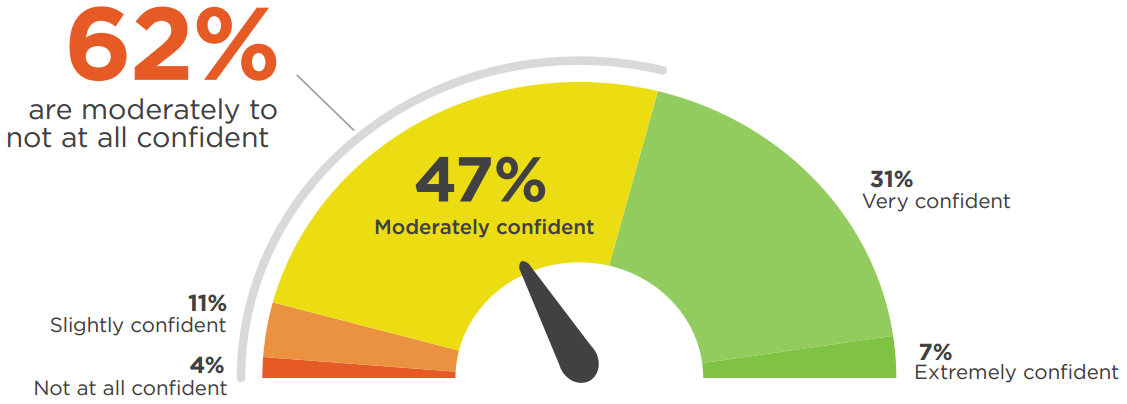
CONFIDENCE IN SECURITY
Latech, فناوری لاجورد تکوین, لاتک
Over half of cybersecurity professionals (62%) are moderately confident to not at all confident in their organization’s overall security posture – presenting a significant opportunity for security staff and vendors to improve overall confidence in their organizations’ security capabilities. Only 38% of respondents expressed a high degree of confidence in their organization’s security posture. Forty-seven percent are moderately confident and 15% are only slightly or not at all confident – presenting a significant opportunity for security staff and vendors to improve overall confidence in their organizations’ security posture.
Q: How confident are you in your organization’s overall security posture?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTIONION
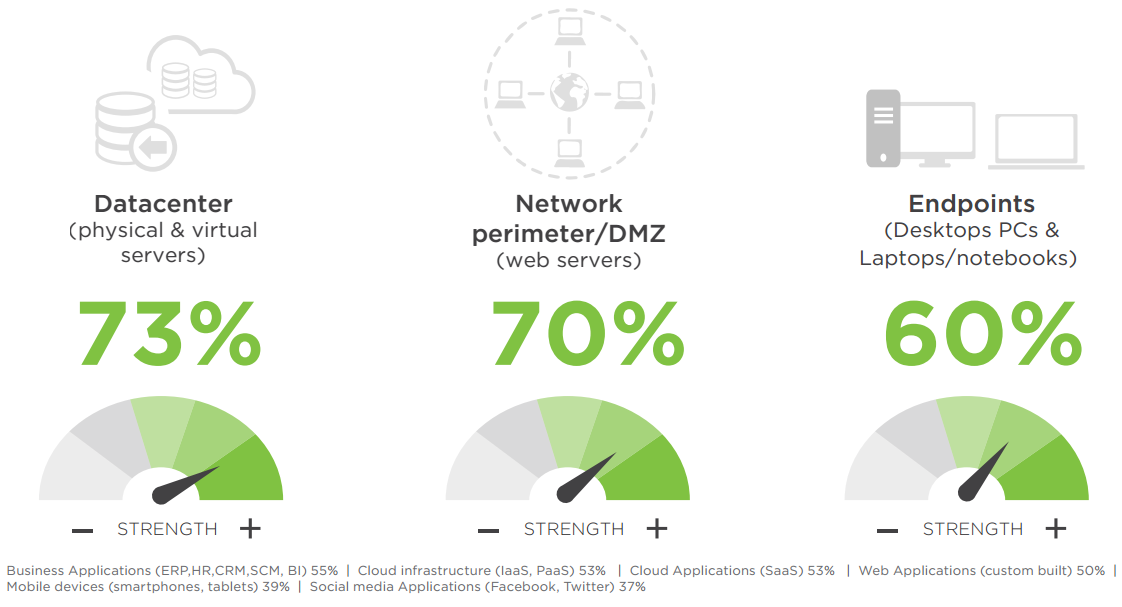
SECURITY STRENGTH
Latech, فناوری لاجورد تکوین, لاتک
Today’s distributed, multi-tier IT environments can be quite complex and challenging to secure. Organizations have the highest confidence in the security strength of their data centers (73%), network perimeter (70%), and end-points (60%). In contrast, respondents have the lowest confidence in social media and mobile security.
Q: How would you rate your organization’s overall security strength (ability to resist cyber threats) in each of the following areas?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
CYBERATTACK INCIDENTS
Latech, فناوری لاجورد تکوین, لاتک
Cybersecurity professionals observed a wide range of cybersecurity incidents over the past 12 months, ranging from zero to hundreds of attacks per organization. On average, cyber experts became aware of 8 cyberattacks in their company in the previous 12 months.
Q: How many times do you estimate that your organization has been compromised by a successful cyberattack within the past 12 months?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
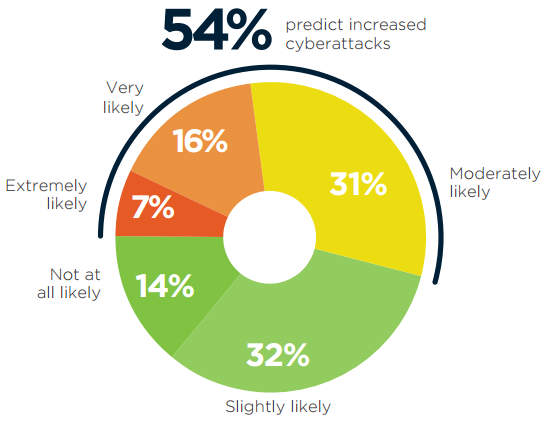
Looking ahead, we asked cybersecurity professionals about their expectations regarding future cyberattacks impacting their organization. Almost a quarter of professionals (23%) assess the probability of future attacks as very or extremely likely. Thirty-one percent say a successful attack is moderately likely. Surprisingly, 46% are confident that their organization is only slightly or not at all at risk of successful cyberattacks in the next 12 months.
Q: What is the likelihood that your organization will become compromised by a successful cyberattack in the next 12 months?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
BIGGEST SECURITY THREATS
Latech, فناوری لاجورد تکوین, لاتک
When it comes to specific threat vectors, cybersecurity professionals are most concerned about phishing attacks, malicious insiders, and malware.
Q: Please rate your overall concern for each of the following cyberthreats targeting your organization.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
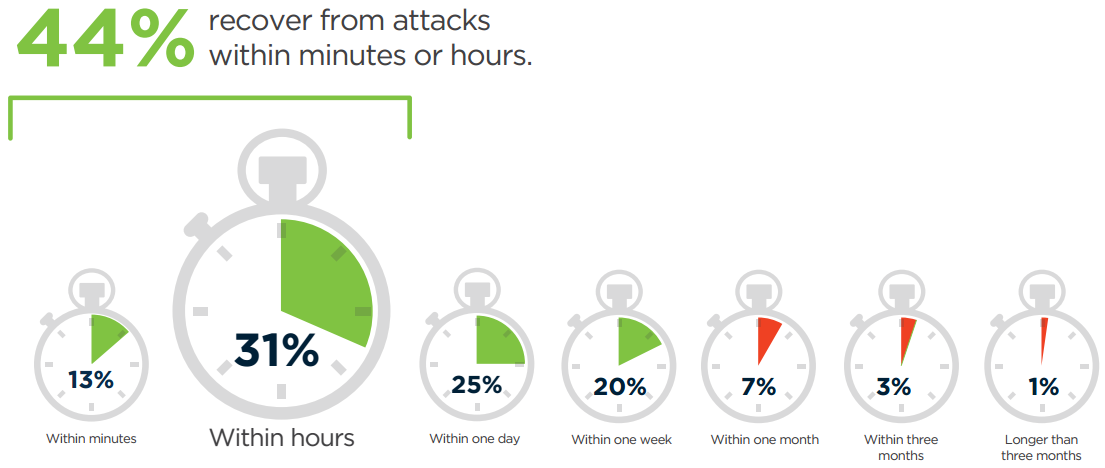
ATTACK RECOVERY TIME
Latech, فناوری لاجورد تکوین, لاتک
One of the biggest security challenges is the detection of sophisticated attacks. While the time it takes to detect an attack varies from company to company, on average it takes over 200 days to detect a breach. Once detected, 44% of cybersecurity professionals claim they typically recover from attacks within minutes or hours, 25% within one day, depending on the severity of the attack.
Q: How long did it take your organization to recover from a cyberattack (on average, once observed)?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
IMPACT OF SECURITY INCIDENTS
Latech, فناوری لاجورد تکوین, لاتک
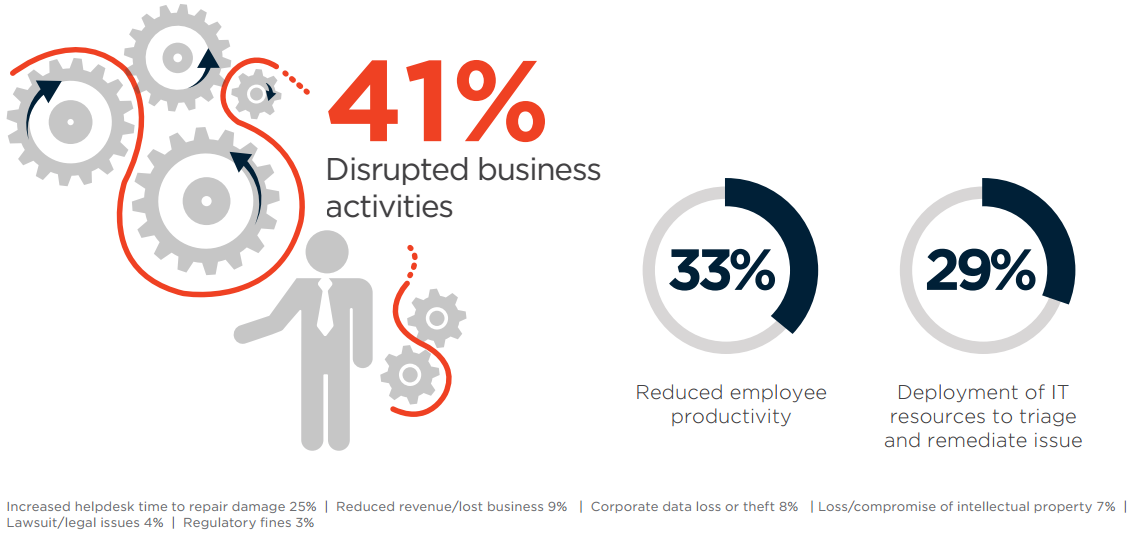
Among the organizations who experienced security incidents, the biggest negative impact comes from disrupted business activities (41%), followed by reduced employee productivity (33%) and the impact on IT staff having to triage and remediate the security incident (29%).
Q: What negative impact have security incidents had on your company in the past 12 months?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
OBSTACLES TO STRONGER CYBERSECURITY
Latech, فناوری لاجورد تکوین, لاتک
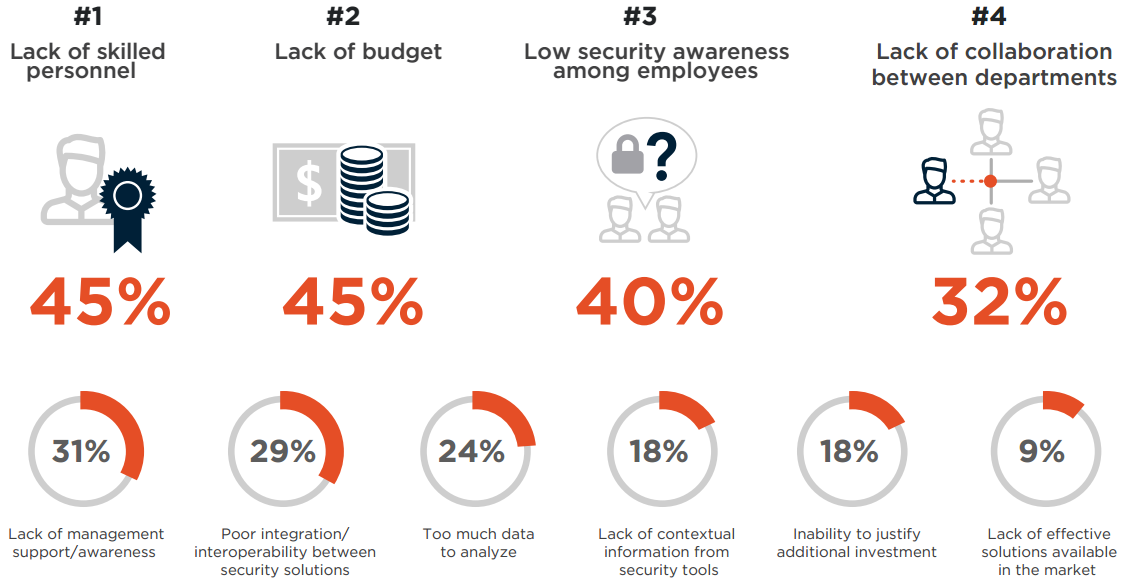
The three biggest obstacles to stronger cybersecurity are all about skills and resources: lack of skilled employees (45%), followed by lack of budget (45%) and lack of security awareness among employees (40%).
Q: Which of the following barriers inhibit your organization from defending against cyberthreats?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
INVESTMENT PRIORITIES
Latech, فناوری لاجورد تکوین, لاتک
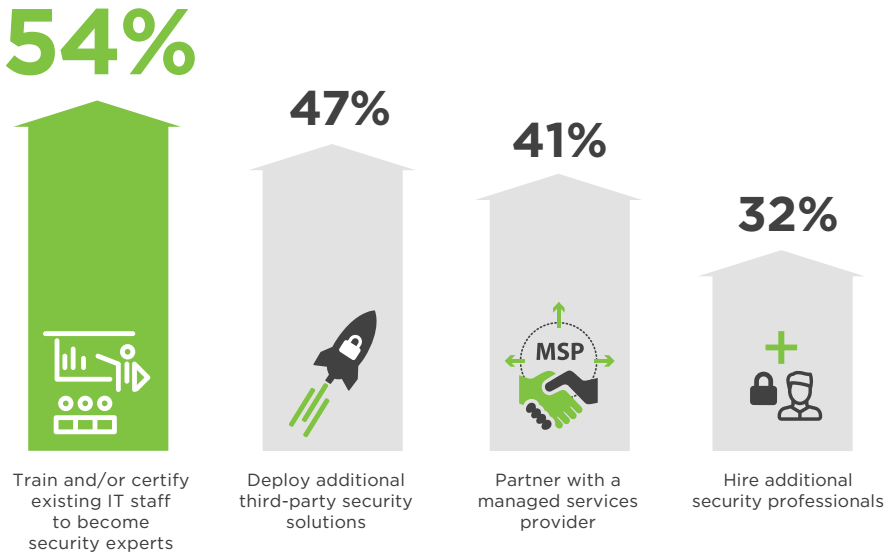
To address evolving security needs in the coming year, a majority of organizations plan to train and certify existing IT staff to become security experts (54%). Forty-seven percent plan to procure and deploy additional security technology solutions, and 41% plan to initiate or expand partnerships with managed services providers.
Q: How do you plan to handle your evolving security needs in the next 12 months?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
SECURITY BUDGET TREND
Latech, فناوری لاجورد تکوین, لاتک
There is no debate on the importance of having the right security solutions. More than half of organizations are boosting their security budget (52%). The average increase that companies are allocating for security is 21%.
Q: How is your security budget changing in the next 12 months?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY,  DATA & FILE PROTECTION
DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
SECURITY BUDGET PRIORITIES
Latech, فناوری لاجورد تکوین, لاتک
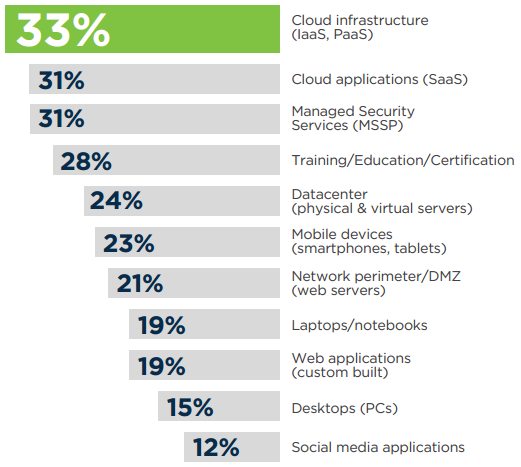
On average, security budgets are 21% of the overall IT budget (excluding headcount). While companies are continually tweaking their budgets, respondents will most likely allocate a higher share of their current security spending on cloud infrastructure, cloud applications, and managed security services.
Q: What IT areas will see an increase in security spend, over the next 12 months? (share of respondents who increase security for each IT tier)
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Security is front and center for respondents. Organizations indicate they will boost future spending levels on a variety of priorities including, cloud infrastructure, cloud applications, managed security services, and training and education.
Q: What is your organization’s security investment priority in each of the following areas over the next 12 months (increasing spend)?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Link to download original report:
Latech, فناوری لاجورد تکوین, لاتک
•THREAT MONITORING, INTELLIGENCE & MANAGEMENT
•CLOUD SECURITY
•MOBILE SECURITY & BYOD
•APPLICATION SECURITY
•ERP SECURITY
•DATA & FILE PROTECTION
•MANAGED & OUTSOURCED SECURITY SERVICES
•SECURITY TRAINING & CERTIFICATION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Security trends in 2017
Latech, فناوری لاجورد تکوین, لاتک
Participants were engaged in survey in regards to below scopes:
Latech, فناوری لاجورد تکوین, لاتک