Security Trends in 2017 – ISC2 report – Data and File Protection
CYBERSECURITY TRENDS
Latech, فناوری لاجورد تکوین, لاتک
2017 SPOTLIGHT REPORT
Latech, فناوری لاجورد تکوین, لاتک
PRESENTED BY (ISC)2
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
OVERVIEW
Latech, فناوری لاجورد تکوین, لاتک
The cybersecurity landscape is changing rapidly, making current and actionable guidance on the latest trends more important than ever.
Latech, فناوری لاجورد تکوین, لاتک
Intro to general trends in ISC2 report:
http://lajvardtech.com/en/security-trends-in-2017-isc2-report-general-trends/
Latech, فناوری لاجورد تکوین, لاتک
DATA & FILE PROTECTION
Latech, فناوری لاجورد تکوین, لاتک
Data is the lifeblood of IT systems, services, and applications. It is also the ultimate target of attacks to steal, sell, manipulate, erase, or corrupt sensitive data and the systems that process it. Data protection needs to encompass a comprehensive strategy for protecting information assets from application/ user errors, malware attacks, machine failure, or facility outages/disruptions along the information lifecycle. This also includes the secure transfer of files, be it for backup or corporate projects. Today, email is still the most common file transfer method for smaller files – yet one of the least secure methods.
Sixty-seven percent of survey respondents ranked data encryption as the most effective means for protecting against cyber security attacks.
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
MOST SENSITIVE INFORMATION
Latech, فناوری لاجورد تکوین, لاتک
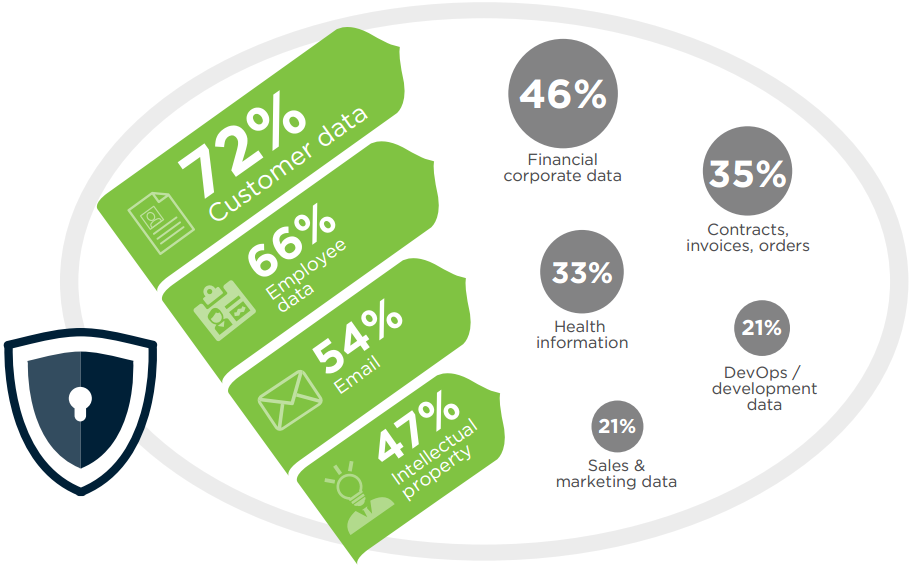
Securing sensitive information is a key concern for all companies, also driven by regulation that require certain sensitive information be protected. Cybersecurity professionals are most concerned about protecting customer data (72%), employee data (66%), and email (54%). Sales and marketing data is considered least critical to be secured (21%). Robust protection of sensitive data at rest and in motion through encryption and other methods is paramount to organizations security strategy.
Q: What types of sensitive data are you most concerned about protecting?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
FILE TRANSFER CHALLENGES
Latech, فناوری لاجورد تکوین, لاتک
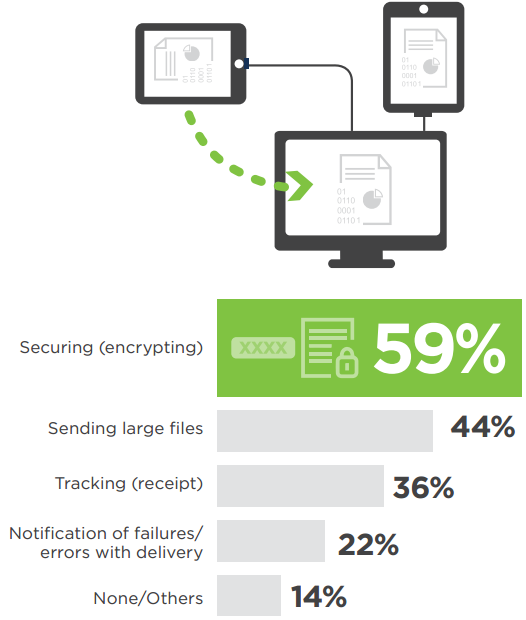
Security is the number one concern (59%) when transferring files, followed by sending large files (44%) and tracking file transfer success (36%).
Q: Which challenges do you face when transferring files?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
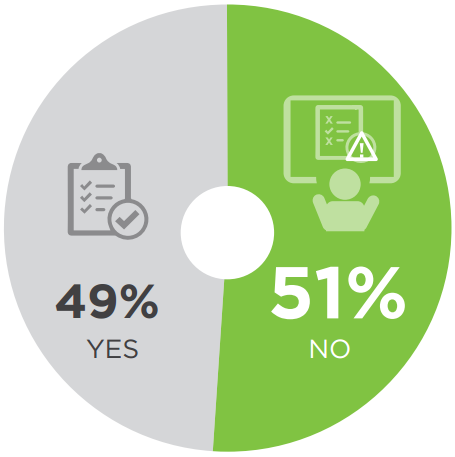
Over half of IT security professionals confirm they lack the tools to prove compliance related to transfer of sensitive files. Secure file transfer solutions should include not only proper file encryption and access controls but also detailed audit logs for maintaining compliance – ideally automated as to reduce the potential for human error.
Q: If your file sharing practices were audited for regulatory compliance, do you have the tools you need to streamline the process?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
FILE EXCHANGE METHODS
Latech, فناوری لاجورد تکوین, لاتک
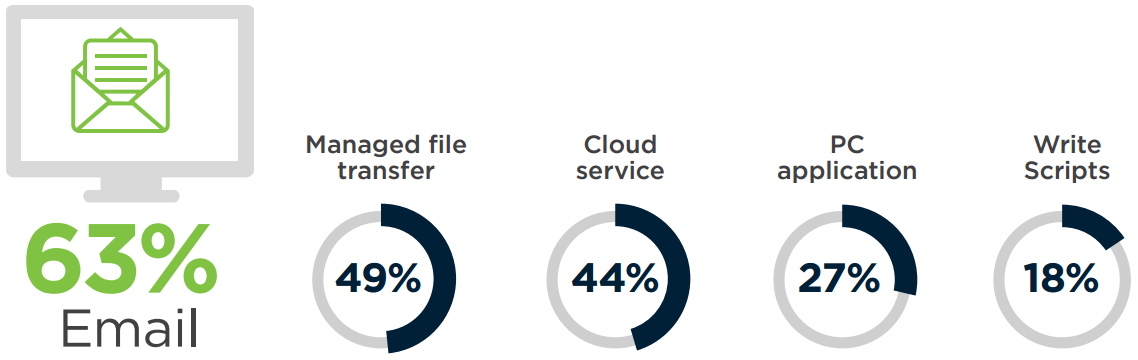
Email is still the most common file transfer method for smaller files (63%). This is a red flag as unsecured email is both prone to security risk and difficult to track for auditing purposes. For larger files, managed file transfer is the next most popular (and more secure) choice (49%), followed by cloud services such as Dropbox, WeTransfer, or YouSendIt (44%).
Q: How do you currently exchange files?
Latech, THREAT MONITORING, INTELLIGENCE & MANAGEMEN, APPLICATION SECURITY, DATA & FILE PROTECTION
Latech, فناوری لاجورد تکوین, لاتک
Latech portfolio to meet requirements in Data and File Protection
Cisco Email Security – FireEye SandBox – PaloAlto WildFire
Latech, فناوری لاجورد تکوین, لاتک
Security trends in 2017
Latech, فناوری لاجورد تکوین, لاتک
Participants were engaged in survey in regards to below scopes:
Latech, فناوری لاجورد تکوین, لاتک